Overview
The Kafka Access page provides a centralized interface to:- Create and manage Kafka users with authentication credentials
- Configure IP safe listing for enhanced security
- Define granular ACLs for topic and consumer group access
- View proxy endpoints for connecting to your Kafka cluster
- Search and filter users by username or IP address
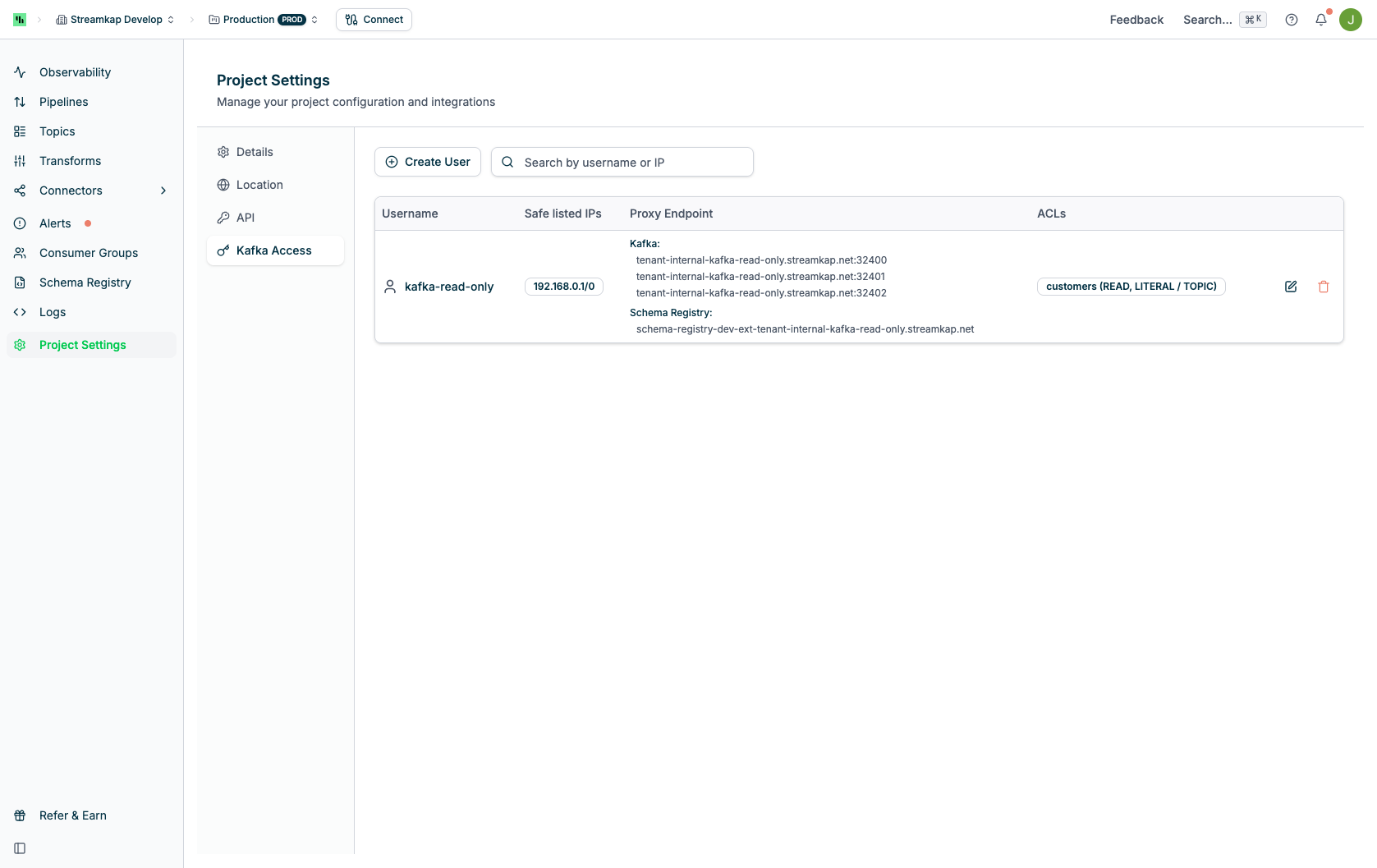
Table Columns
The Kafka Access table displays the following information:- Username: The Kafka username (lowercase only)
- Safe listed IPs: CIDR-notated IP addresses allowed to connect
- Proxy Endpoint: The Kafka proxy connection endpoints (host:port)
- ACLs: Summary of configured Access Control Lists showing resource name, operation, pattern type, and resource type
Quick Actions
Each user row includes action buttons on the right:- Edit (pencil icon): Modify user settings, password, IPs, and ACLs
- Delete (trash icon): Remove the Kafka user
Creating a Kafka User
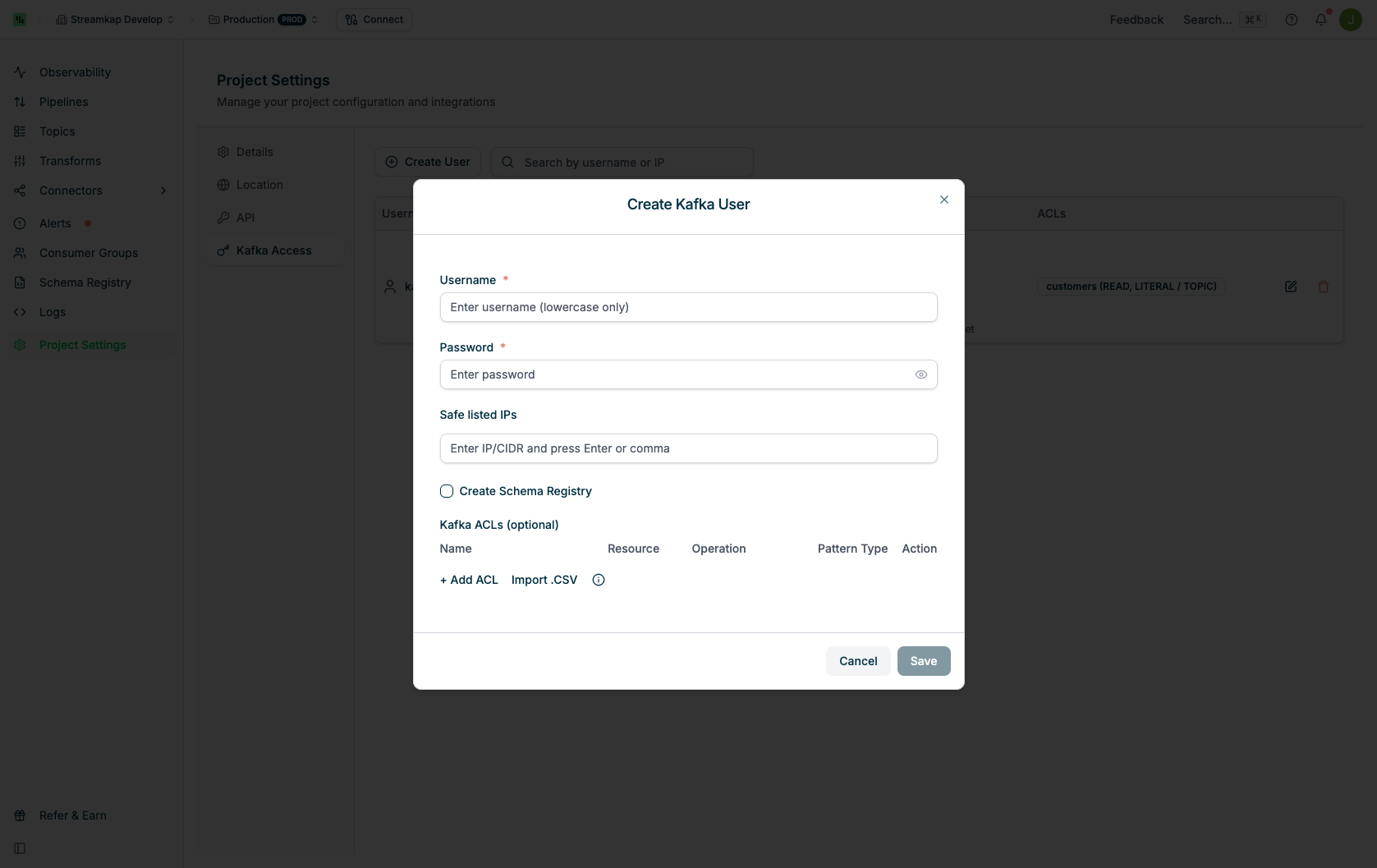
To create a new Kafka user:Enter Username
Provide a unique username (lowercase characters only).
Usernames must be lowercase and unique within your project.
Configure Safe listed IPs (Optional)
Add IP addresses or CIDR ranges that are allowed to connect with this user.
- Enter IP/CIDR notation (e.g.,
192.168.1.0/24) - Press Enter or comma to add multiple IPs
- Leave empty to allow connections from any IP
Configure ACLs (Optional)
Define Access Control Lists to control what this user can access.Click + Add ACL to add a new rule. For each ACL, specify:
- Name: The resource name (topic name, consumer group name, or pattern)
- Resource: The type of resource
TOPIC: Kafka topicsGROUP: Consumer groupsCLUSTER: Cluster-level operationsTRANSACTIONAL_ID: Transactional IDsDELEGATION_TOKEN: Delegation tokens
- Operation: The allowed operation
READ: Consume from topics or read group offsetsWRITE: Write data to topicsCREATE: Create topics or other resourcesDELETE: Delete resourcesALTER: Modify resource configurationsDESCRIBE: View resource metadata (required by many clients alongside READ/WRITE)CLUSTER_ACTION: Perform cluster-level actionsDESCRIBE_CONFIGS: View configurationsALTER_CONFIGS: Modify configurationsIDEMPOTENT_WRITE: Idempotent writesALL: All operations
- Pattern Type: How the resource name is matched
LITERAL: Exact match (e.g., specific topic name)PREFIXED: Matches resources starting with this prefix
Import .CSV: You can bulk import ACL rules from a CSV file by clicking the “Import .CSV” button.
Editing a Kafka User
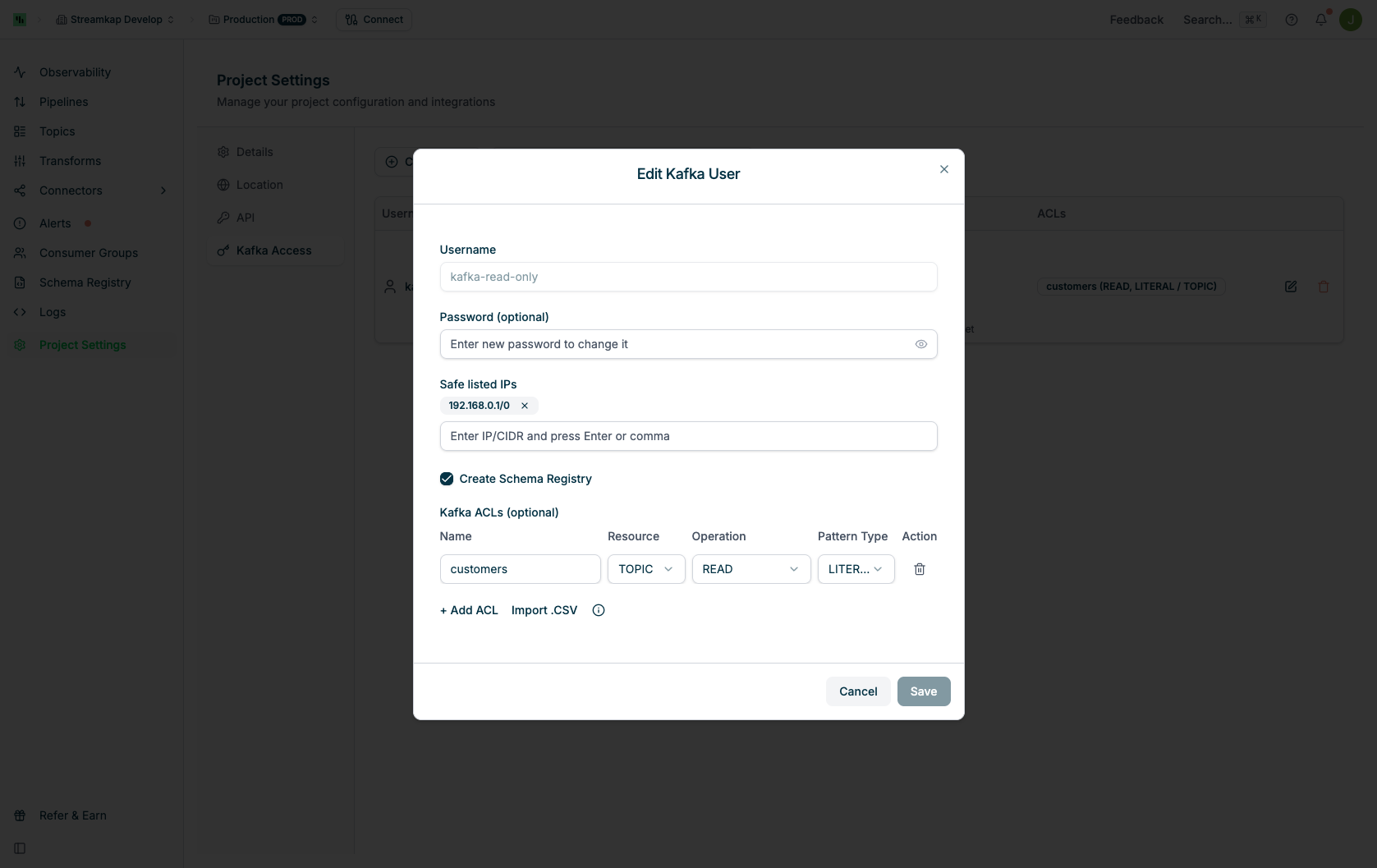
To modify an existing Kafka user:- Click the Edit button (pencil icon) for the user you want to modify
- The Edit Kafka User dialog will appear showing current settings
Editable Fields
- Username: Display only (cannot be changed after creation)
- Password (optional): Enter a new password to change it, or leave empty to keep the current password
- Safe listed IPs: Add or remove IP addresses/CIDR ranges
- Kafka ACLs: Add, modify, or remove ACL rules
Deleting a Kafka User
To remove a Kafka user:- Click the Delete button (trash icon) for the user
- Confirm the deletion when prompted
Searching and Filtering
Use the search bar to quickly find users:- Search by username
- Search by IP address (full or partial match)
Connecting to Kafka
Once a user is created, you can connect to Kafka using the proxy endpoints displayed in the table.Connection Details
- Bootstrap Servers: Use the proxy endpoints from the “Proxy Endpoint” column
- Security Protocol:
SASL_SSL - SASL Mechanism:
PLAIN - Username: The Kafka username you created
- Password: The password you set for the user
Example Connection Configuration
Project Selection
The Kafka Access page is project-specific. You can switch between projects using the project selector in the navigation bar. Each project has its own set of Kafka users and proxy endpoints.ACL Best Practices
When configuring ACLs, follow these best practices:- Principle of Least Privilege: Grant only the minimum permissions required for each user
- Use Literal Matches: When possible, use
LITERALpattern type for specific topic names to avoid over-permissioning - Separate Users by Function: Create different users for producers, consumers, and administrative tasks
- Combine READ and DESCRIBE: Consumers typically need both
READ(for data) andDESCRIBE(for metadata) - Consumer Groups: Don’t forget to grant
READaccess to consumer groups (resource typeGROUP) for consumer applications - Testing: Test ACL configurations in a development environment before applying to production
Common ACL Patterns
Read-Only Consumer
- Resource:
TOPICwith topic name - Operation:
READ - Pattern Type:
LITERAL
- Resource:
GROUPwith consumer group name - Operation:
READ - Pattern Type:
LITERALorPREFIXED
Producer
- Resource:
TOPICwith topic name - Operation:
WRITE - Pattern Type:
LITERAL
Admin User
- Resource:
CLUSTER - Operation:
ALL - Pattern Type:
LITERAL
Security Considerations
- Rotate Passwords Regularly: Change user passwords periodically
- Use IP Safe listing: Restrict access to known IP ranges when possible
- Monitor Access: Check audit logs regularly for unauthorized access attempts
- Remove Unused Users: Delete users that are no longer needed
- Strong Passwords: Use complex passwords with a mix of characters
Troubleshooting
Connection Refused
If you cannot connect to Kafka:- Verify the proxy endpoints are correct
- Check that your IP address is safe listed (if configured)
- Confirm the username and password are correct
- Ensure your firewall allows outbound connections to the proxy ports
Permission Denied
If you receive permission denied errors:- Review the user’s ACLs to ensure they have the required permissions
- Check that the ACL resource name matches your topic/group name exactly (for
LITERALmatches) - Verify the operation type includes what you’re trying to do (e.g.,
READfor consuming)
User Not Found
If a user appears in the list but cannot authenticate:- Verify you’re connecting to the correct project endpoints
- Check that the password was set correctly
- Try editing the user and resetting the password
Related Documentation
- Projects - Managing Streamkap projects
- Topics - Working with Kafka topics
- Organisation Security - Overall security settings